MFT Gateway is a hosted Software as a Service (SaaS) solution that enables file exchange over the AS2 or SFTP protocol, without the need to install or maintain.
- Blog
- Must know facts on AS2
AS2
Must know facts on AS2
Check out our blog article to learn must-know facts about AS2 and how it works. Learn more about AS2!

Lahiru Ananda
Published: 30 Sep 2022

What is AS2?
For those who want to know “What is AS2?”, AS2 is an abbreviation for Applicability Statement 2 - a secure B2B transfer protocol that allows businesses to exchange Electronic Data Interchange (EDI) documents or other data, such as XML, CSV, or plain text documents with their trading partners. AS2 defines a reliable and secure mechanism to transfer structured business data via the Internet using HTTP/S (hypertext transport protocol secure), the same protocol nearly every website uses. In simple terms, AS2 is an “envelope” for sensitive business data, allowing it to be sent securely through a point to point client-server connection.
History
AS2 is a second-generation EDI specifications, published by the Internet Engineering Task Force (IETF) in 2002 as a replacement for their AS1 protocol introduced in the late 1990s. AS1 was a first-generation EDI specification that used email protocol for secure data transfers.
Why AS2?
There are some other protocols available for B2B communication such as FTP, SFTP, and FTPS. But in contrast to those traditional B2B protocols, AS2 offers a secure, efficient and simple-to-use trading environment without a need for proprietary devices, software, value-added networks, or expensive private networks.
Business Value
- With lower costs and universal internet connectivity, AS2 allows you to implement EDI with partners worldwide that have little EDI infrastructure - with minimal infrastructure on your end as well.
- AS2 is a universal solution; once it is established and tested, one does not have to reinvent the wheel.
- AS2 reduces the cost of transactions by using the internet for EDI file transfers rather than using expensive VANs.
- Save time and eliminate errors by turning manual processes into automated processes.
Technological Advantages
- AS2 can be used to transport any type of document. While EDI X12, EDIFACT, and XML are common, any mutually agreed format may be transferred.
- AS2 leverage the internet, infrastructure for AS2 is the ability to share data securely via the internet. If you can share data securely via the internet, you already have much of the infrastructure for AS2.
- There are no practical limitations on transaction sizes via the internet, and AS2 includes features explicitly for managing large transfers - which means unlimited EDI data transferring.
Key features
AS2 protocol defines that a message can be encrypted, digitally signed, and compressed before sending it to the recipient over an SSL tunnel (optionally) making the file transfers very secure. The recipient can send a Message Disposition Notification (MDN) to the sender, ensuring the message was delivered successfully. MDN can be digitally signed and will contain a checksum value that the sender will use to verify that the message received was identical to what was sent.
Encryption - AS2 uses Asymmetric Cryptography, also known as public-key cryptography, for message encryption. Sender encrypts message content with the recipient’s public key certificate to keep the data secure. Encrypted content can only be decrypted by using the corresponding private key - held only by the recipient - ensuring only the intended recipient will be able to interpret the content.
Digital Signatures- A digital signature is used to verify the identity of the message sender. The sender should sign a message using his private key which then allows the recipient to verify the authenticity of the sender. The recipient verifies the signature by using the sender’s public key certificate. The recipient can also sign his MDN to ensure the identity of the recipient’s system. These digital signatures are used for message integrity and non-repudiation of origin.
Compression - Compression can be added to decrease the overall size of the message in order to improve transmission time.
Message Disposition Notification (MDN) - MDN, which is commonly referred to as a receipt, will make sure that the recipient received the message; and if digitally signed, it also verifies the identity of the recipient. The receiver can send back the receipt immediately over the same connection as a synchronous MDN - or he can send back the receipt later on a new connection, perhaps after the message has been processed - known as asynchronous mode.
Message Integrity Check(MIC) - After a message has been received, the recipient will calculate a checksum of the message using a hashing algorithm like MD5, SHA1, or SHA256. This calculated value is referred to as the MIC, and it will be sent back to the sender with the MDN. The sender will calculate a checksum using the same algorithm to make sure that the message sent is identical to the message that was received by the recipient. Non-repudiation of Receipt - The use of signatures on the message and receipt creates a Non-Repudiation of Receipt (NRR) event, which is considered legal proof of delivery.
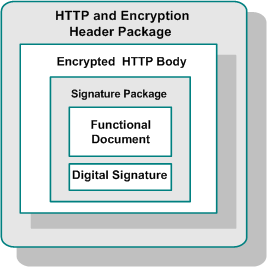
AS2 Message Format
The basic structure of an AS2 message consists of a MIME format inside an HTTP message, with a few additional AS2-specific HTTP headers.
An AS2 message conforms to the following structure:
- HTTP header package: RFC2616/RFC2045
- Encryption package: RFC2633 (application/pkcs7-mime)
How AS2 works
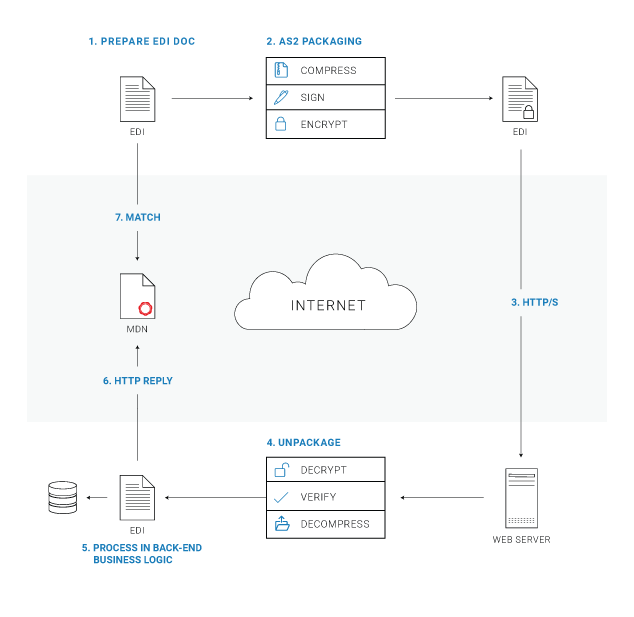
AS2 follows a fairly straightforward process. Fist of all you need to have an AS2 software that acts as both a client (for message sending) and a server (for message receiving). There are some open-source AS2 implementation such as OpenAS2 and Mendelson AS2 for this purpose, Also, you can always go with an enterprise-grade SaaS AS2 application like Aayu Technologies LLC AS2 Gateway which provides a B2B trading platform for organizations - with the ability to configure AS2 stations and trading partners with a nice, simplified and intuitive interface concealing the underlying complexities.
EDI document preparation - Message content could be prepared in a standard EDI format to send over AS2. This is an optional step as AS2 can send documents in any format.
AS2 packaging - Content to be sent via AS2 can undergo three types of transformation:
- Compression: The document may be compressed using a compression algorithm to reduce the size of the transported data
- Signature: The data is typically signed using the sender’s private key to ensure the sender’s identity
- Encryption: The data is typically encrypted using the receiver’s public encryption key to ensure the security of the content during the transmission process.
Message Delivery - The message is securely transmitted over HTTP/S using file transmission software or services.
AS2 Unpacking - The receiver will unpack the message to retrieve the EDI document. If the data was encrypted, the document will be decrypted using the receiver’s private key. If signed, the signature on the document is verified using the sender’s public key. If the document was compressed, it will be decompressed.
EDI Processing - The AS2 receiver passes the unpacked EDI document to any back-end process that handles the data to perform any additional business logic.
MDN Reply - The receiver uses AS2 or EDI software to send a message confirmation receipt to the sender. The receiver will calculate the MIC as described before, and will send it along with the MDN.
MDN Processing - The sender validates the receipt signature and compares the returned MIC against the one originally calculated to make sure the content was delivered without any corruption or tampering.
Conclusion
AS2 is a universal method for B2B data transmission, used by millions of businesses worldwide, including most major retailers, such as Amazon and Walmart. When properly implemented, AS2 is a system for reliably and securely transferring files between trading partners. If you are interested in AS2, this will be a good starting point for your AS2 journey. Also, If you are interested in the AS2 technical background feel free to go through RFC 4130.
👉 New to AS2? Do not worry. Click here to explore our blog posts to learn more about AS2

Talk to an EDI Expert
Join hundreds of organizations already taking full control of their B2B AS2 communications with our trusted solutions. Contact us today to tailor a solution that fits your specific AS2 EDI needs.
Related Articles
View All BlogsExplore our product stack
Try before you buy with a 30-day Free Trial
No commitment, all value. Try the AS2 Solution Risk-Free and discover how our solutions can transform your business workflows. No credit card required.
Explore Your Possibilities
Elevate AS2 Communications with our EDI and AS2 Solutions
See how our AS2 and EDI solutions can simplify your integrations, boost efficiency, and keep you compliant—request a personalized demo today.