MFT Gateway is a hosted Software as a Service (SaaS) solution that enables file exchange over the AS2 or SFTP protocol, without the need to install or maintain.
- Blog
- Data Security Solutions: How to Secure File Transfers
SFTP | AS2
Data Security Solutions: How to Secure File Transfers
Share your EDI data using encryption and secure file transfer protocols

Kumudika Rupasinghe
Published: 05 Jun 2024

Introduction
Data protection in transit is important as data is usually considered less secure while in motion. Hence, secure file transmission is a vital part of effective data protection of an organization, especially when dealing with sensitive data. Managed File Transfer (MFT) software provides a reliable and secure method for transmitting files between systems and usually supports multiple protocols to securely exchange files. AS2 (Applicability Statement 2) and SFTP (Secure File Transfer Protocol) are two such widely used protocols. Let’s discuss how MFT software ensures secure file transmission using these two protocols.
AS2 for secure file transfer
AS2 is a specification on how to transmit structured Business-to-Business (B2B) data securely and reliably over the Internet. This is commonly used in industries such as retail, pharmaceutical, and logistics to exchange trading documents like purchase orders, invoices, and shipment notices in Electronic Data Interchange (EDI) format.
AS2 protocol-level security
HTTPS for Transport Security
AS2 typically runs over HTTP or HTTPS. When using HTTPS, SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols are employed to secure the communication channel. This provides additional encryption and ensures that data cannot be intercepted or tampered with during transmission.
Signing and Encryption
AS2 uses signing to ensure the authenticity, integrity and non-repudiation of the transmitted data and encryption to protect confidentiality. AS2 protocol uses public key cryptography (aka asymmetric cryptography) for signing and encryption.
AS2 message sender and receiver will obtain a keypair for each, containing a private key and a public key signed by a trusted entity, and exchange the public keys with each other before the AS2 transmission. The private key will be securely stored with the owner, to ensure that it does not get compromised.
As an MFT software, Aayu Technologies’ MFT Gateway provides the facility to users to manage existing certificates or generate self-signed certificates required for AS2 transmissions.
In the AS2 transmission, prior to message sending, the sender computes a hash of the payload called the Message Integrity Check (MIC), and saves the computed MIC value to be verified at the end of the AS2 transmission process. Then the original payload is signed using the message sender’s private key file. Here we create a hash of the payload and then encrypt this hash using the sender’s private key, resulting in a digital signature. The entire signed payload is then encrypted using the recipient’s public key and packaged into an AS2 message, and sent to the recipient’s AS2 server.
Aayu Technologies’s MFT Gateway supports multiple algorithms for encryption and signing and allows customization for each trading partner. Moreover, it provides the ability to reject insecure (unencrypted/unsigned) incoming AS2 messages without further processing.
Once the message is transmitted to the receiver, the message recipient uses his private key to decrypt the message. Assuming the receiver’s private key has not been compromised, this ensures that the message will only be decrypted by the intended recipient (confidentiality) and ensures integrity by verifying that the message has not been altered during the transmission. The receiver then uses the sender’s public key file to verify the digital signature on the received payload and confirm the identity of the message sender, along with non-repudiation. Moreover, the signature verification process ensures the file is not tampered during the transmission (integrity).
Acknowledgement Receipts: Message Disposition Notification (MDN)
Once the recipient decrypts and verifies the signature, an acknowledgement will be composed and sent by the recipient to the original message sender as proof of delivery. These MDNs can be either synchronous or asynchronous. Apart from the other message processing details, this MDN includes the following two elements as part of the AS2 security measures.
-
Message Integrity Check (MIC): The message recipient will compute a cryptographic hash value (MIC) over the received payload and include that value in a header of the MDN. Once the MDN is received, the original message sender will verify whether the stored MIC matches the received MIC, to ensure that the payload has not been altered during the transmission.
-
Digital Signature: Ensuring non-repudiation, the message receiver will digitally sign the MDN using his private key and include it as a digital signature, adding a layer of reliability to the transmission process.
MFT Gateway facilitates all these MDN-level security measures and allows customized configurations for each trading partner.
SFTP for secure file transfer
SFTP is an extension of the Secure Shell (SSH) protocol and is used for securely transferring files over a network. Unlike FTP (File Transfer Protocol), which transmits data in plaintext, the underlying SSH protocol in SFTP includes data encryption, data integrity protective services, and server authentication.
SFTP protocol-level security
Authentication
SFTP supports multiple authentication methods, including password-based authentication, SSH key authentication, and multi-factor authentication (MFA). SSH key authentication is particularly secure, as it involves using cryptographic key pairs where the private key is kept secure by the user and the public key is shared with the server. Following these best practices, MFT Gateway allows SFTP access via username and private-key-based authentication.
Encryption
SFTP encrypts the entire session, including both the data being transferred and the authentication process. It uses encryption algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) to ensure that data cannot be intercepted or read by unauthorized parties. The encryption is symmetric, meaning the same key is used for both encryption and decryption, but this key is exchanged securely using asymmetric encryption methods.
Data Integrity
Data integrity in SFTP is maintained using cryptographic hash functions and MAC (Message Authentication Code) algorithms. These mechanisms ensure that any data corruption or tampering during transmission is detected by the receiving party.
Access Control and Permissions
SFTP servers provide robust access control mechanisms, allowing administrators to define user permissions for files and directories. This ensures that only authorized users can access, modify, or transfer specific files, adding an additional layer of security.
Combining AS2 and SFTP for Enhanced Security
An MFT solution like MFT Gateway that supports both AS2 and SFTP can provide versatile and robust security for file transfers. Organizations can choose the protocol that best fits their specific needs, or even use both protocols in different scenarios to maximize security.
-
Flexibility: By supporting both AS2 and SFTP, MFT software offers flexibility to handle different types of data exchanges. For example, AS2 might be used for EDI transactions with trading partners, while SFTP could be used for regular file backups, internal data transfers or automated file transfers. Moreover, the users can build up business relationships with a wider range of trading partners that use AS2 or/and SFTP for their B2B transactions.
-
Layered Security: Using both protocols can provide layered security. For instance, an organization might encrypt a file using AS2 before transmitting it over SFTP, adding an extra layer of encryption and integrity checks. MFT Gateway’s SFTP Integration feature can be used to perform AS2 file transmissions via SFTP.
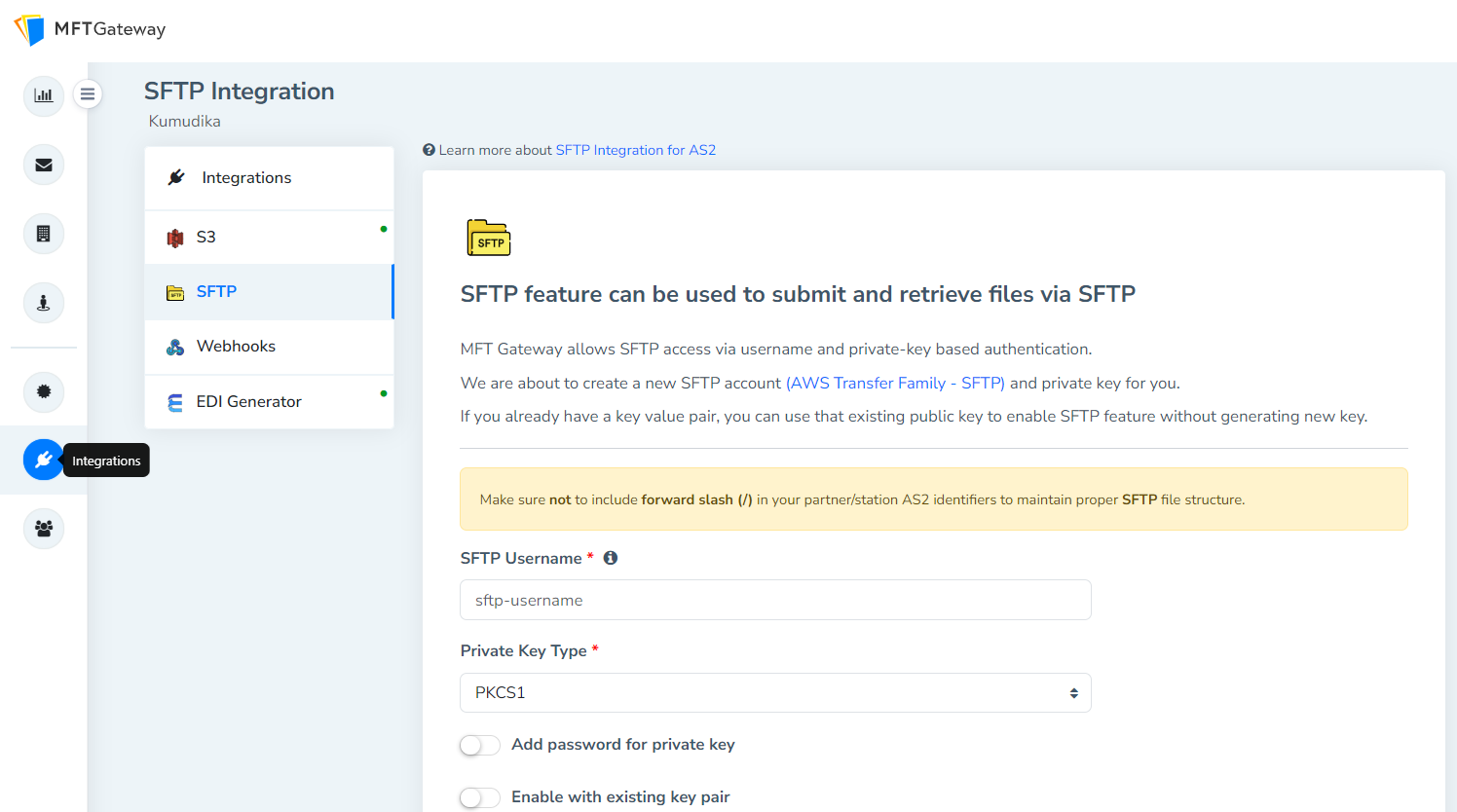
- Compliance Many industries have specific compliance requirements for data transmission. Supporting both AS2 and SFTP ensures that the MFT software can meet diverse regulatory standards, such as HIPAA for healthcare data or PCI DSS for payment card information.
Conclusion
As data security solutions in MFT software, AS2 and SFTP leverage robust security features. AS2 provides encryption, digital signatures, MDNs, and HTTPS transport security to protect data during transit. SFTP offers encrypted sessions, strong authentication methods, data integrity checks, and access control to safeguard file transfers. By supporting both protocols, MFT software can cover extensive security and compliance requirements. The combination of both protocols ensures that whether the data is being transmitted between trading partners or within an organization’s internal network, it remains protected from unauthorized access and tampering.

Talk to an EDI Expert
Join hundreds of organizations already taking full control of their B2B AS2 communications with our trusted solutions. Contact us today to tailor a solution that fits your specific AS2 EDI needs.
Related Articles
View All BlogsExplore our product stack
Try before you buy with a 30-day Free Trial
No commitment, all value. Try the AS2 Solution Risk-Free and discover how our solutions can transform your business workflows. No credit card required.
Explore Your Possibilities
Elevate AS2 Communications with our EDI and AS2 Solutions
See how our AS2 and EDI solutions can simplify your integrations, boost efficiency, and keep you compliant—request a personalized demo today.





















































































































































































