MFT Gateway is a hosted Software as a Service (SaaS) solution that enables file exchange over the AS2 or SFTP protocol, without the need to install or maintain.
- Blog
- Enhance Cybersecurity with Managed File Transfer
MFT
Enhance Cybersecurity with Managed File Transfer
Today’s organizations face a wide range of cybersecurity threats, each employing unique tactics and having various consequences. The most common categories of cyberattacks are described as follows.

Sampavi Sriparan
Published: 25 Jun 2024

Today’s organizations face a wide range of cybersecurity threats, each employing unique tactics and having various consequences. The most common categories of cyberattacks are described as follows.
Most common types of cyber security attacks
1. Phishing and Smishing:
-
Phishing involves tricking individuals into clicking on malicious links in emails or on websites to reveal sensitive information, such as login credentials or personal details. These emails often appear to originate from legitimate sources.
-
Smishing is similar to phishing but uses text messages instead of emails. Attackers send fraudulent messages pretending to be from trusted companies to trick individuals into revealing sensitive information, such as credit card numbers or passwords.
2. Ransomware is a type of malware that blocks access to a victim’s personal data until a ransom is paid.
3. Malware is short for malicious software, which can be used to steal, encrypt, or delete sensitive data, disrupt operations, or gain unauthorized access to network systems.
4. Accidental Data Loss or Leakage occurs when sensitive information is unintentionally exposed or lost. This can result from employee errors, such as sending emails to the wrong recipient, software misconfigurations, or losing devices with unencrypted data. These incidents can lead to significant data breaches.
5. Third-Party Exposure refers to the cybersecurity risks an organization faces from its vendors and partners. These third parties may lack strong security measures, making them potential weak points. If compromised, they can expose the organization’s sensitive data.
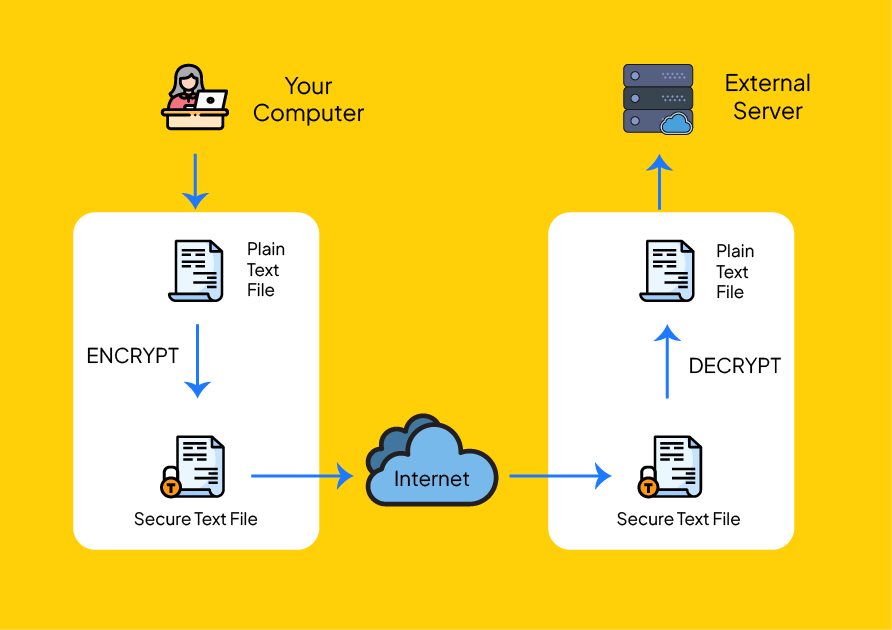
Ensuring the secure transfer of data over the internet is crucial for organizations. Managed File Transfer (MFT) solutions provide a secure, reliable, and compliant method for transferring data, safeguarding its integrity and confidentiality during transit.
How MFT helps mitigate cybersecurity risks
Managed File Transfer (MFT) is a software solution that facilitates the sharing of business-critical and sensitive data. To mitigate cyber attacks during document transfers between organizations, secure file transfer is essential. Secure file transfer solutions use encryption with industry-standard network protocols to protect data both in transit and at rest.
Our Managed File Transfer Gateway (MFTG) solutions facilitate the secure sharing of business documents by utilizing AS2 and SFTP protocols. These protocols ensure that data is encrypted and protected during transmission, safeguarding sensitive information from cyber threats and unauthorized access.
Secure file transfer via AS2 Protocol
AS2 is a protocol that ensures secure data transmission using encryption, digital signatures, and acknowledgments. It encrypts data with advanced encryption algorithms, making intercepted data unreadable without the decryption key. Digital signatures verify the sender’s identity and ensure data integrity, preventing tampering. AS2 provides non-repudiation through digital signatures and Message Disposition Notifications (MDNs), ensuring the sender cannot deny sending the message, and the receiver cannot deny receiving it. The receiver sends an MDN to confirm successful receipt and processing, ensuring the sender knows the message was delivered correctly.
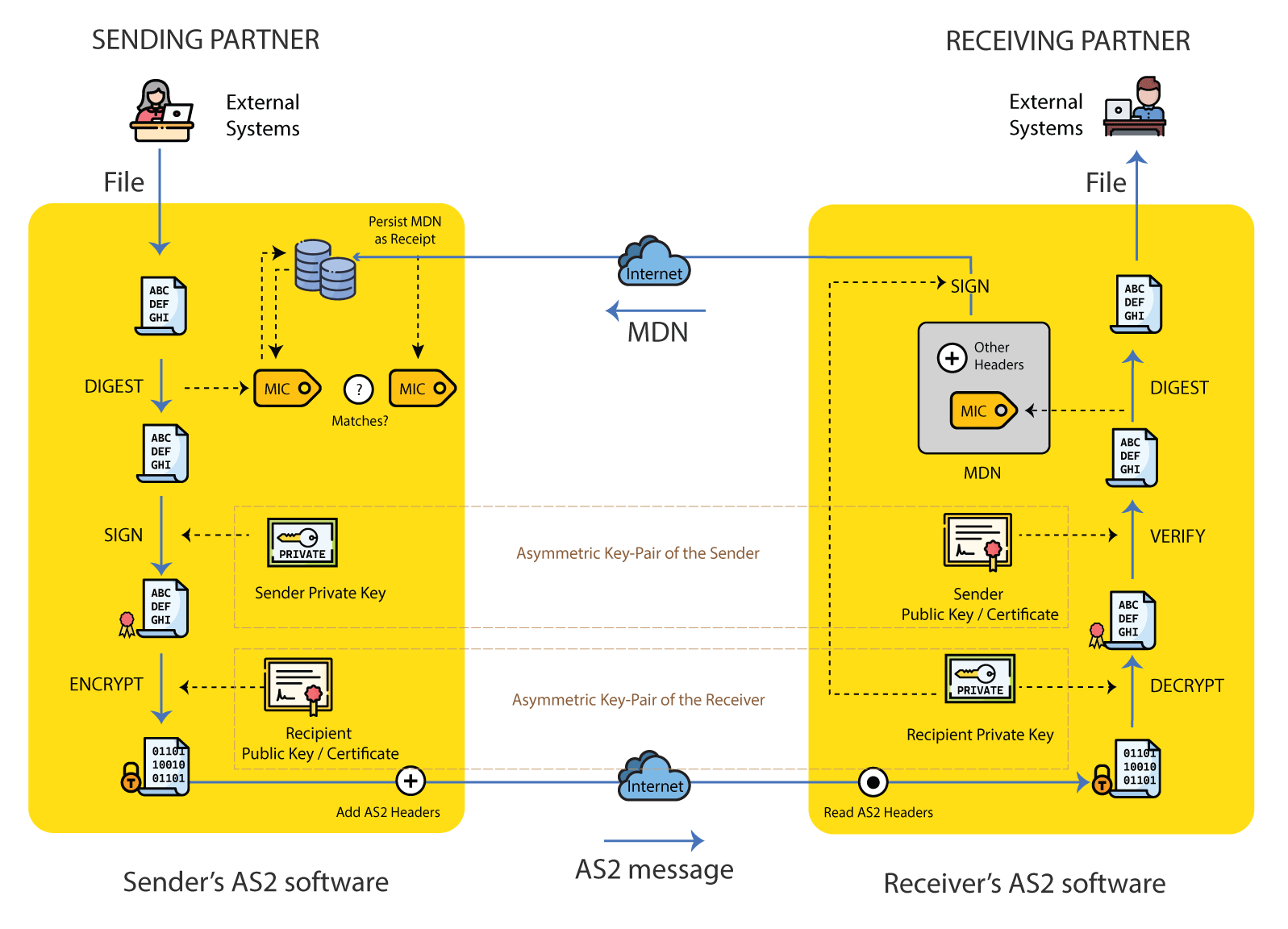
Secure file transfer via SFTP Protocol
MFT Gateway also offers SFTP (Secure File Transfer Protocol) to facilitate secure document exchanges. As an extension of the SSH (Secure Shell) protocol, SFTP offers robust file transfer capabilities across networks and is widely adopted for secure transfers both within and between organizations.
Key security features of SFTP include:
1. Public Key Authentication: This method uses cryptographic keys for authentication, more secure than traditional password authentication, and reducing the risks of unauthorized access and password theft.
2. Granular Access Control: SFTP enables administrators to set precise permissions for users and groups, minimizing the risk of unauthorized access to sensitive files.
How does MFT Gateway ensure security?
Hosted on AWS
MFT Gateway is hosted on AWS, enabling organizations to leverage robust security features and tools to mitigate various cyber threats. AWS comprehensive security framework ensures data protection, threat detection, and compliance, thereby enhancing the overall security posture of the MFT Gateway.
Multi-tenant SaaS solution
Being a multi-tenant SaaS solution, each tenant or account within the MFT Gateway is assigned its own unique S3 bucket, ensuring data isolation and minimizing the risk of unauthorized access between accounts.
Utilizes AWS Identity and Access Management (IAM)
Using AWS Identity and Access Management (IAM), MFT Gateway sets precise permissions for each bucket, ensuring that only authorized users can access specific data. AWS provides server-side encryption (SSE) for S3 buckets, ensuring data is encrypted when stored.
AWS S3’s server-side encryption
Additionally, S3’s server-side encryption and versioning capabilities ensure that data is protected and that older versions can be restored if the current data is lost or becomes unusable due to a cybersecurity threat such as ransomware. Restricting who can delete or modify data, and using bucket policies to control access at the bucket level, further enhances security.
AWS Resource Monitoring
AWS also tracks API calls and user activity across its infrastructure, providing an audit trail for security and compliance. Monitoring AWS resources and applications with tools like CloudTrail, CloudWatch and GuardDuty offers real-time insights and alerts for unusual activity, ensuring continuous oversight and quick response to potential security incidents.
Key Points
-
The MFT Gateway (MFTG) effectively prevents cyber attacks by integrating secure protocols like AS2 and SFTP with AWS robust security infrastructure.
-
AS2 ensures secure data transmission over the internet using encryption, digital signatures, and acknowledgment receipts, protecting against data tampering, unauthorized access, and repudiation.
-
SFTP enhances security through strong encryption, public key authentication, and granular access controls, safeguarding data during transfer and reducing the risk of credential-based attacks.
-
Hosting MFTG on AWS further strengthens its security posture. AWS provides a comprehensive security framework that includes features such as separate S3 buckets for each tenant, server-side encryption, IAM for precise permission management, and versioning capabilities to recover from accidental deletions or ransomware attacks. AWS’s monitoring and logging tools, such as CloudTrail and CloudWatch, ensure real-time visibility and auditing of user activity, helping detect and respond to suspicious behavior promptly.
In conclusion, by leveraging the security strengths of AS2 and SFTP protocols along with AWS’s advanced security features, MFT Gateway offers a robust defense against cyber threats, ensuring secure, reliable, and compliant data transfers for organizations.

Talk to an EDI Expert
Join hundreds of organizations already taking full control of their B2B AS2 communications with our trusted solutions. Contact us today to tailor a solution that fits your specific AS2 EDI needs.
Related Articles
View All BlogsExplore our product stack
Try before you buy with a 30-day Free Trial
No commitment, all value. Try the AS2 Solution Risk-Free and discover how our solutions can transform your business workflows. No credit card required.
Explore Your Possibilities
Elevate AS2 Communications with our EDI and AS2 Solutions
See how our AS2 and EDI solutions can simplify your integrations, boost efficiency, and keep you compliant—request a personalized demo today.