MFT Gateway is a hosted Software as a Service (SaaS) solution that enables file exchange over the AS2 or SFTP protocol, without the need to install or maintain.
- Blog
- How to Send and Receive AS2 Messages: A Step-by-Step Guide
EDI
How to Send and Receive AS2 Messages: A Step-by-Step Guide
Learn to securely send and receive AS2 messages step-by-step. Ensure reliable EDI exchange with encryption, MDNs, and best AS2 configuration practices.

Sampavi Sriparan
Published: 16 Jul 2025

Applicability Statement 2 (AS2) is a widely used protocol that allows businesses to securely and reliably transfer data over the internet. It is most particularly common in EDI (Electronic Data Interchange) where a business communicates with its trading partners in terms of documents such as orders or invoices. AS2 provides data integrity and confidentiality by relying on encryption and digital signatures. Data encryption provides confidentiality throughout the transmission whereas the digital signature confirms the identity of the message sender and secures the message against alteration maintaining data integrity. Files are transmitted as AS2 messages over the transport layer of HTTP or HTTPS. AS2 supports Message Disposition Notifications (MDNs) that act as acknowledgment messages to indicate whether the message has been received and processed successfully.
In this article, we will walk you through the steps you must follow to exchange AS2 messages with your trading partners in a step-by-step guide.
How to Send and Receive AS2 Messages
With an idea of what AS2 is and how it works, we can now go through the steps of sending and receiving AS2 messages. AS2 communication involves several important steps, establishing AS2 connection, exchanges of certificates, endpoint configuration, and handling acknowledgments. Every step is vital in the process of secure, reliable, and compliant transfer of files among trading partners. This is a simple step-by-step procedure to assist you in the process.
1. AS2 Communication Setup
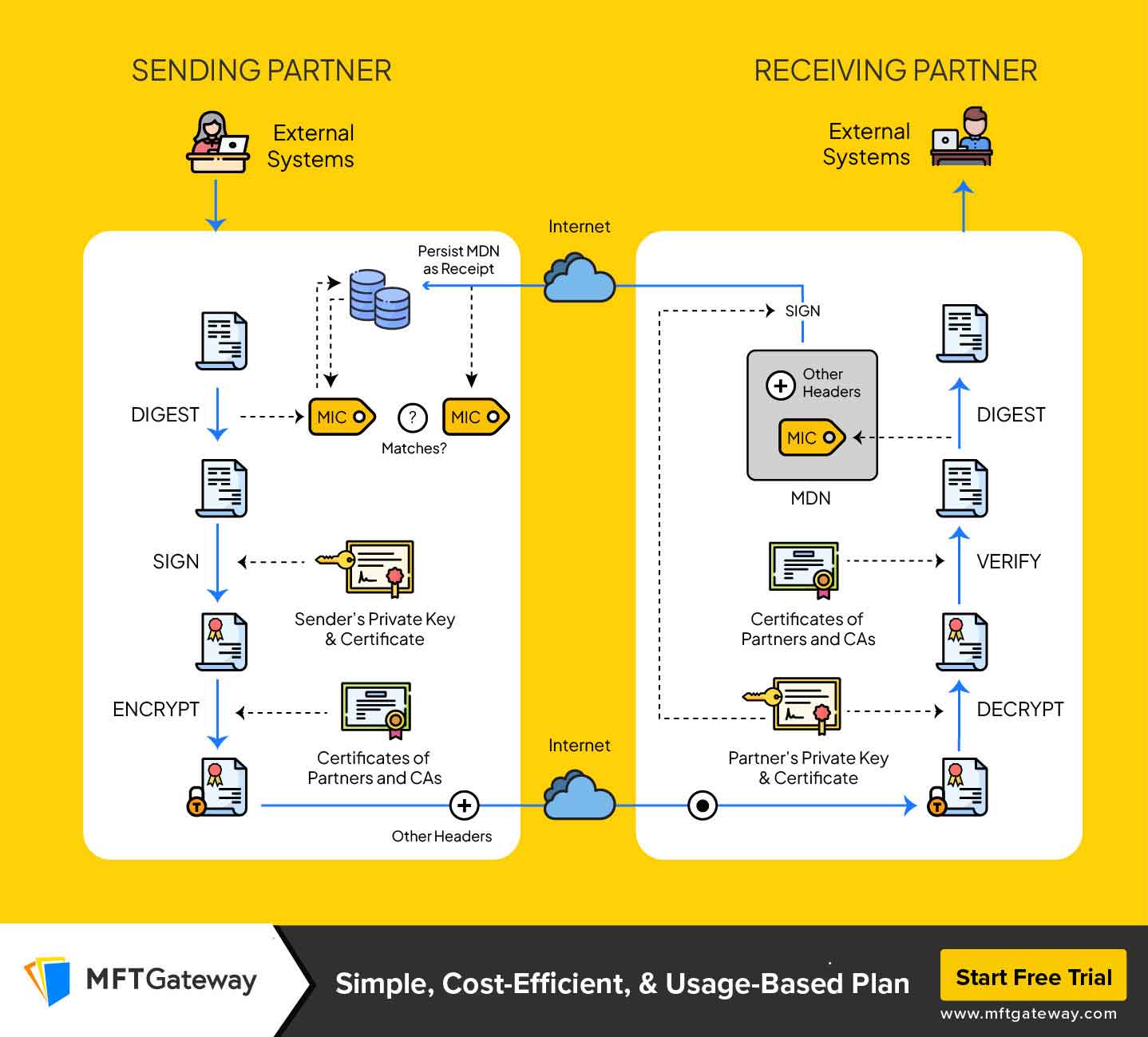
AS2 communication requires the configuration of both sides of the communication parties that are, sender and receiver to communicate reliably and securely. Both sides need to identify themselves using a unique AS2 identifier (AS2 ID) and AS2 endpoint URL, the URL which is used to send or receive messages. An important component of the configuration is the exchange of security certificates to be used in encryption and digital signatures, normally an X.509 public certificate is distributed to the partners to support secure communications.
The protocol also requires both partners to configure on the parameters like encryption algorithms (e.g. AES or 3DES), signature algorithms (e.g. SHA-256), compression (in case used), and MDN mode (synchronous or asynchronous). When the configuration is complete, the sender creates an AS2 message around the business document (such as an EDI 850 or XML file , or any other) and adds security parameters before sending it to the partner AS2 endpoint. The receiving system reads the message and on demand, sends back the MDN as a confirmation of receipt.
Effective AS2 connection ensures secure exchange of data, compliance with regulation, and the ability to connect with trading partners such as Walmart, Amazon or government agencies. This configuration can be simplified by managed file transfer solutions which provide user-friendly interfaces and automation.
2. Prepare the Files for Transmission
After the AS2 connection is established on both the side of sender and receiver, the sender needs to prepare the files to be transmitted. This is the process of choosing or creating the document to transmit- an EDI 850 purchase order, an XML file, or any other business documents. Once the files are selected, there are a few security measures that the sender may apply. The file size can be reduced to facilitate more efficient transmission through compression, usually by ZLIB. This is followed by the digital signing of the file with the sender of the information using their own certificate in order to make the receiver identify the sender and to guarantee the integrity of the file. Lastly, the file is encrypted with the receiver’s public certificate to make it secure. These are the necessary steps in making an AS2 file transfer secure, reliable, and able to pass both business and compliance standards.
3. Send the AS2 Message
Once the file is correctly prepared, i.e. compressed, signed and encrypted (as necessary), it can be sent. The AS2 software now takes over by wrapping the file into a properly formatted AS2 message. This wrapping involves creation of a MIME message that contains the payload (your business document) and the required headers and security information.
The AS2 message is transported then via HTTPS to the destination AS2 endpoint URL of the recipient. This guarantees that the transport layer is also safe besides the encryption at the message level. AS2-specific header lines are added during transmission that contain metadata like sending and receiving AS2 ID, the message ID, the content type and whether a Message Disposition Notification (MDN) is requested.
This step is the essence of sending an AS2 message, here is where the transfer of the actual file occurs. Now this message is securely being sent across the internet and provided everything is set up correctly, it arrives at the AS2 system of the recipient ready to be decrypted and processed. This is where proper logging and monitoring can be done to ensure a successful send and is useful in troubleshooting in case of issues.
4. Receive the AS2 Message
When an AS2 message is received at the recipient end, it starts with the AS2 system verifying the incoming message so as to prove that it is authentic and not manipulated. In case the message is encrypted, then it is decrypted with the help of the private certificate of the recipient so that the message can be readable. In a case of digital signature to the message, the system authenticates the signature by use of the sender’s public certificate to ensure that the sender is the one who sent it and that the message integrity is guaranteed.
After validation and decryption, the payload is obtained and then stored securely, e.g. an EDI file, XML or any other business document. In addition to this, AS2 system records important transaction information, including message ID, sender and receiver IDs, timestamps and status indicators, which are crucial to audit trails and troubleshooting.
The file is then passed to the internal systems of the recipient to be further processed after the storage. This may include parsing an EDI file and delivering it to an ERP system and initiating workflows or connecting to downstream business applications. This will be finalization of the secure delivery process which will see that the business data is in operational use.
5. Send or Receive MDNs
The exchange of an MDN (Message Disposition Notification) is a crucial step that comes after receiving and processing an AS2 message. An MDN notifies the sender of the message delivery’s outcome and serves as a digital acknowledgement or receipt. It verifies that the AS2 message was successfully received, that the digital signature (if used) was correctly validated, and that the message was processed and decrypted without any errors.
MDNs are essential to building reliability and trust in AS2 communication. They act as official evidence that the transaction took place, the data arrived unaltered, and the source was confirmed. This is particularly crucial in sectors where data traceability and regulatory compliance are crucial, such as retail, healthcare, and logistics.
There are two types of MDNs: synchronous and asynchronous. The instant the recipient processes the message, a synchronous MDN is returned in the same HTTP session. This offers almost instantaneous confirmation. An asynchronous MDN, on the other hand, is returned via a different HTTP request and is usually employed in situations where message processing takes longer, the recipient is located behind a firewall, or the network configuration is more complicated.
Conclusion
Once everything is set up, sending and receiving AS2 messages can be a quick, safe, and standardised method of exchanging important business files. Every step is essential to guaranteeing dependability and compliance in your B2B integrations, from message delivery and MDN handling to partner configuration and encryption.
If you’re looking for a reliable and manageable solution, our MFT Gateway (MFTG) and AS2 Gateway (AS2G) provide full support for every facet of AS2 communication, such as:
- AS2 configuration with certificate management and partner onboarding.
- Encrypting, compressing, and signing messages to ensure secure transmission and message receipt.
- Automated synchronous and asynchronous MDN management for guaranteed delivery.
- Integrated dashboards and alerting to track the flow of messages and promptly detect errors.

Talk to an EDI Expert
Join hundreds of organizations already taking full control of their B2B AS2 communications with our trusted solutions. Contact us today to tailor a solution that fits your specific AS2 EDI needs.
Related Articles
View All BlogsExplore our product stack
Try before you buy with a 30-day Free Trial
No commitment, all value. Try the AS2 Solution Risk-Free and discover how our solutions can transform your business workflows. No credit card required.
Explore Your Possibilities
Elevate AS2 Communications with our EDI and AS2 Solutions
See how our AS2 and EDI solutions can simplify your integrations, boost efficiency, and keep you compliant—request a personalized demo today.