MFT Gateway is a hosted Software as a Service (SaaS) solution that enables file exchange over the AS2 or SFTP protocol, without the need to install or maintain.
- Blog
- Different Keystore Types for B2B File Transfer | Q4 2025
MFT
Different Keystore Types for B2B File Transfer | Q4 2025
Learn about different keystore types for secure B2B file transfer, updated for Q4 2025. Explore JKS, PKCS12, BKS, and how they protect cryptographic keys and certificates.

Samadhi Kariyawasam
Modified: 28 Oct 2025

In this digital age, cryptographic keys and certificates play an important role in information security.
What are keys and certificates?
A key is a string of characters used in the encryption and decryption of any important information that has to retain its confidentiality, integrity, and authenticity. Depending on the type of encryption, the key used may vary.
- Secret key for symmetric encryption: The same string of characters is used in the encryption and decryption of the information.
- Key pair for asymmetric encryption (public key cryptography): This encryption involves a key pair (public key and private key) where one key (public key) is used in the encryption of the data and the other key (private key) is used in the decryption of the data.
A certificate/digital certificate is a document containing a public key that is signed by a trusted third party (a certificate authority) to guarantee the authenticity of the key.
What is a keystore?
While the keys ensure the safety of data, a keystore is used to safely store the keys by giving managed access to the keys and certificates that are stored in them. There are different types of keystores, such as JKS, PKCS12, and BKS. While their primary function is to store keys and certificates, there can be slight differences between the keystore types.
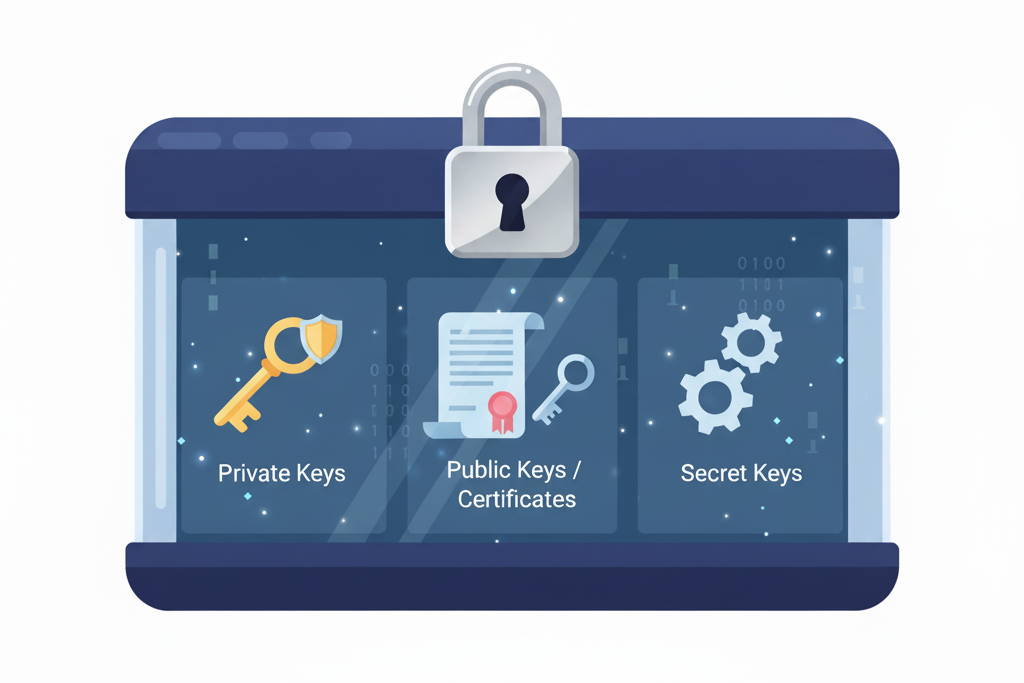
What are stored in a keystore
Before moving on to the keystore types, it’s important to understand the types of keys that a keystore can store.
- Private keys: Any entity that uses the public key cryptography holds a private key that is securely stored and only accessible to its owner. It is used to decrypt data encrypted by its public key and to sign to prove data authenticity.
- Public keys/certificates: A public key is the key that is open to the public out of the key pair, and it is used to encrypt data and verify the sender’s signature.
- Secret Keys: Keys used in symmetric encryption, where the same key is used for the encryption and decryption.
Securing a Keystore
To secure the keys and certificates inside a keystore, there are multiple methods used.
- Encryption
- Password protection
- Protection Against Brute-Force Attacks
Keystore types
JKS
JKS (Java Keystore) is the proprietary keystore implementation provided by the SUN provider; it was the default keystore in SUN until Java 9. JKS keystore files have the .jks extension.
-
Pros: JKS keystore is one of the most widely used keystore types.
-
Cons: JKS keystores can only be used within a Java application. They cannot be used to store secret keys.
-
Security: In JKS, private keys are protected with the password by first SHA-1 hashing and salting the password recursively until the number of bytes is equal to the private key. Then, the password byte stream is XORed against the private key and stored. Furthermore, to check the integrity of the stored private key, an authenticator tag is used. This authenticator tag is made of the SHA-1 hash of the password and private key. Finally, to check the integrity of the whole keystore, the SHA-1 hash of the keystore password, the phrase “Mighty Aphrodite,” and the encoded keystore entries are hashed together.
JCEKS
JCEKS (Java Cryptography Extension Keystore) is the proprietary keystore implementation provided by the SunJCE provider.
-
Pros: JCEKS keystores are much more secure when compared to JKS keystores when storing private keys because they use Triple DES encryption.
-
Security: In JCEKS keystore, to encrypt individual key entries, the password is hashed using MD5, with a 64-bit salt in 200,000 iterations (PBKDF1). It is further protected by the TripleDES encryption algorithm with 3 keys in CBC mode. Moreover in JCEKS, integrity checks can only be done for the whole keystore. And it uses the same method with the phrase ‘Mighty Aphrodite’ as JKS to do this integrity check.
PKCS12
PKCS12 (Public Key Cryptography Standards #12) is a standard and universal keystore type. PKCS12 keystore files usually have the extension pfx or p12.
-
Pros: Unlike Java-specific JKS, PKCS12 is supported across a wide variety of platforms and tools. PKCS12 keystores also support the storage of secret keys in addition to private and public keys and certificates.
-
Security: The PKCS#12 standard is flexible in choosing the encryption algorithm. By choosing a stronger algorithm like AES block cipher, the stored keys will be more secure when compared to JKS or JCEKS keystores.But in PKCS#12 keystores, there is no integrity check for individual entries but the whole keystore.
Basically, PKCS#12 is a better keystore option than the above legacy keystores, and it is the default keystore type in Java from JDK version 9 and higher.
BKS
BouncyCastle Keystore (BKS) is the keystore implementation provided by the BouncyCastle cryptography library.
- Security: Like the other keystores, it also derives the stored keys using the keystore password that the user provides, using the PBKDF function, and the hashing function is repeated in a random number (between 1024 and 2047)
- of iterations. The TripleDES algorithm is also used in this key encryption.
UBER
The Bouncy Castle UBER keystore also uses the PBKDF1 algorithm with a random number of iterations of the SHA-1 hash function. But one difference of the UBER keystore is that it uses the TwoFish block cipher instead of the Triple DES algorithm used by BKS. Also, it encrypts the whole keystore again using a password with the same PBKDF1 and TwoFish algorithms. To do the integrity check of the keys, a SHA-1 hash of the whole keystore before the encryption is used.
BCFKS
BCFKS is a FIPS-approved keystore provided by BouncyCastle. It uses the password with the PBKDF2 function to derive the stored key. The hashing function used in the key derivation of BCFKS is the SHA-512, and the hash function is repeated 16,384 times.

Simplify your AS2 connections and make B2B communication faster, safer, and easier than ever.

Talk to an EDI Expert
Join hundreds of organizations already taking full control of their B2B AS2 communications with our trusted solutions. Contact us today to tailor a solution that fits your specific AS2 EDI needs.
Related Articles
View All BlogsExplore our product stack
Try before you buy with a 30-day Free Trial
No commitment, all value. Try the AS2 Solution Risk-Free and discover how our solutions can transform your business workflows. No credit card required.
Explore Your Possibilities
Elevate AS2 Communications with our EDI and AS2 Solutions
See how our AS2 and EDI solutions can simplify your integrations, boost efficiency, and keep you compliant—request a personalized demo today.